IHSE’s mission-critical KVM solutions - When uncompromising security is required (Sponsored)
This article is brought to you by IHSE
KVM stands for Keyboard, Video and Mouse, referring to the familiar workplace computer input and output devices. IHSE’s mission-critical system solutions extend the distance between the computer and peripheral devices (keyboard, monitor, mouse). Allowing users to select between different source devices to create more comfortable and efficient working environments and streamlined workflows.IHSE offers KVM products for the switching, sharing, extension and conversion of all types of computer signals, including analog and digital video and audio, USB and SDI video; applicable to all markets. Long distances are bridged by Cat X, fiber or mixed cabling, depending on security requirements and applications. IHSE KVM solutions stand for upmost security, preventing unauthorized access or injection of malware and guarding data security.
Protected computer access
IHSE’s Draco vario KVMA Isolated Secure Extender enables remote computer access in high-security environments that must meet stringent cyber security specifications – such as government, defense and critical infrastructure. Provisioned users can control multiple computers and systems using the same set of peripherals (keyboard, monitor, mouse) without exposing confidential data to attack. Extenders are equipped with specific shielding layers on both the hardware and integral firmware to prevent eavesdropping and signal detection from Radiofrequency (RF) Radiation. Restricted hardware access also protects from bulk data theft (e. g. via USB flash drive) or the injection of malware.
Common Criteria certified; NIAP PP4.0 and EAL4+ compliant
Developed in collaboration with security experts at HighSecLabs (HSL), the Draco vario KVMA Isolated Secure Extender is designed to meet the most stringent government and defense specifications. The devices comply with the highest IT security standards of the NIAP PP4.0 Common Criteria Protection Profile for Peripheral Sharing Devices version 4.0 and ISO/IEC 15408 Common Criteria (CC) EAL4+. This ensures up-to-date protection against data leakage.
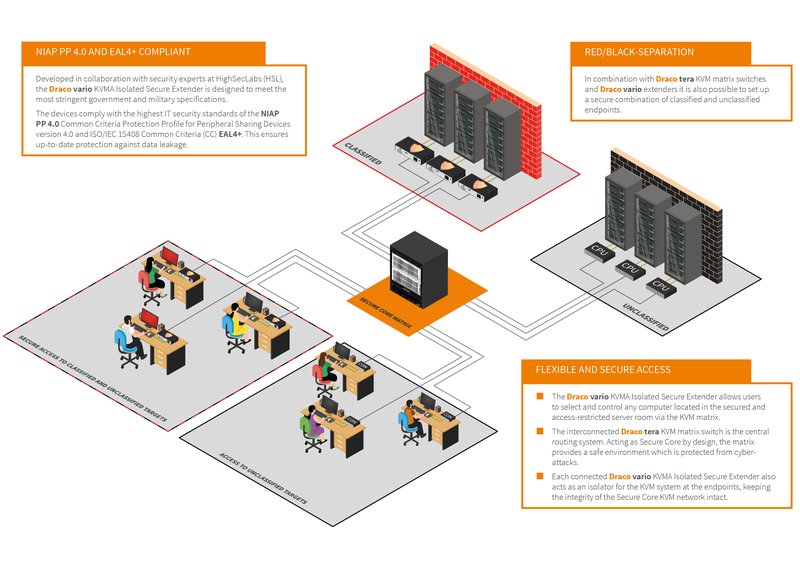
Separation of Red and Black environments
The Draco vario KVMA Isolated Secure Extender allows provisioned users to select and control any computer located in the secured and access-restricted server room via the KVM matrix. Each connected Draco vario KVMA Isolated Secure Extender also acts as an isolator for the KVM system at the endpoints, keeping the integrity of the Secure Core KVM network intact. In combination with Draco tera KVM matrix switches and Draco vario extenders it is also possible to set up a secure combination of classified and unclassified endpoints. The IHSE KVM system enables precise user access rights management as required in government and defense installations with separated classified and unclassified environments.
High investment security
The system supports most current display resolutions and is already prepared for many future formats. This means that the Draco solution represents a long-lasting, high-ROI investment that will scale with user demands for many years to come.

Above: Draco vario KVMA Isolated Secure Extender
Total connectivity and flexible switching
Draco tera KVM matrix switches enable controlled access to (and management of) any size of computer installation. Sources can be accessed, switched and shared instantly by users. Any connected user console (consisting of keyboard, mouse, monitor or other peripherals) can access any computer within the network with defined access rights. Switches include comprehensive features such as multi-screen control and cross-conversion between AV signals and transmission media (Cat X and fiber). The Draco tera range extends from 8 to 576 non-blocking assignable ports. With mixed operation over copper and fiber cables the switches handle all types of computer signals including USB, audio and video (HD, 4K, 8K above). Draco tera is designed for 24/7 mission-critical operation with extensive redundancy features and hot-swap option of components. Users can instantaneously access any computer-based control and information system at the best possible video quality. Acting as Secure Core by design, the matrix provides a safe environment which is protected from cyber-attacks.
More from Industry Spotlights
-
![The power of partnership: GDMS–UK deepens cooperation with the British Army]()
The power of partnership: GDMS–UK deepens cooperation with the British Army
In Conversation: Shephard's Gerrard Cowan talks to General Dynamics Mission Systems–United Kingdom’s Chris Burrows about how the company's UK TacCIS business is reshaping battlefield communications through sustained customer engagement, accelerated innovation and ecosystem collaboration.
-
![Expanded focus – unleashing the potential of commercial SATCOM for defence]()
Expanded focus – unleashing the potential of commercial SATCOM for defence
In conversation... Intelsat's Ray Lindenmayer talks to Shephard's Gerrard Cowan about the new capabilities advanced commercial SATCOM technologies can provide for military customers, and how industry and government can best work together to achieve maximum effect in orbit.
-
![Enhancing education: How CAE is embracing new technology to boost military training]()
Enhancing education: How CAE is embracing new technology to boost military training
In Conversation... Shephard's Gerrard Cowan talks to CAE's Marc-Olivier Sabourin about how the training and simulation industry can help militaries achieve essential levels of readiness by leveraging new technology, innovative procurement methods and a truly collaborative approach.
-
![Why tactical UAVs are winning on the future battlefield (Podcast)]()
Why tactical UAVs are winning on the future battlefield (Podcast)
In Conversation: In this special edition of the Shephard Defence Podcast, Tony Skinner sits down with Dan Slasky, President and CEO of Aeronautics, to explore how cutting-edge tactical unmanned aerial systems are reshaping today’s battlefields.
-
![Fincantieri’s Vulcano Class: a new era of versatility and innovation in naval operations]()
Fincantieri’s Vulcano Class: a new era of versatility and innovation in naval operations
Logistic support ships (LSS) are essential for sustained naval operations, especially during extended deployments far from home ports.
-
![Need more flexibility in battle management system delivery?]()
Need more flexibility in battle management system delivery?
Systematic’s newest solution, SitaWare BattleCloud, brings greater flexibility to combat information systems and C4ISR.
























